Cybersecurity is no longer a technical afterthought—it’s a business-critical priority. More than three-quarters (76%) of global consumers say that the steps a retailer takes to reassure them about data protection significantly influence their decision to physically visit a store. With cyberattacks becoming more frequent and sophisticated, businesses must take strategic measures to protect their data, operations and reputation.
Recent high-profile cyberattacks have made headlines around the world. In May 2025, a suspected cybercriminal group named Scattered Spider—reportedly composed of predominantly young American and British males, some as young as 14 years old—allegedly targeted UK retailers for extortion.
Cyberattacks are also on the rise in the U.S., and the FBI has issued a warning to major technology companies, encouraging them to tighten up their security. In 2023, the same group attacked several Las Vegas casinos.
What’s more concerning is how these attackers gain access. According to Rafe Pilling, threat intelligence director at Secureworks, these hackers use social engineering techniques to steal and reset passwords: “They understand business processes well and so they’re very good at manipulating people.”
Once inside these systems, hackers gain access to all kinds of business and customer data, including names, contact information and, in certain cases, payment information. It’s no surprise, then, that customers are worried—60% have abandoned an online purchase due to the distrust of payment systems.
Part of the problem lies in security fatigue, while the other part lies in poor processes and the systems in place. “Retailers generally don’t prioritise cyber security in the same way the regulated industries do, and there are more opportunities to target companies in retail and hospitality, manufacturing, and healthcare,” Pilling added.
These incidents underscore a harsh reality: no business is immune to attacks, and the consequences of a breach can be devastating, for both customers and retailers.
Why Certain Businesses Are Prime Targets
Cybercriminals are drawn to particular kinds of businesses for several reasons:
-
Valuable Data: Companies, like retailers, store vast amounts of personal, financial and proprietary information.
-
Complex Digital Ecosystems: The more devices and systems a business uses, the larger the attack surface is, leaving more opportunities to exploit entry points.
-
Third-Party Dependencies: If third-party vendors and contractors don’t have proper systems in place and/or use outdated software, they can introduce vulnerabilities.
-
Financial Motivation: Ransomware and data theft are lucrative for attackers and can be used for extortion or selling on the dark web.
The cost of a data breach can be catastrophic. Beyond immediate financial losses, businesses face regulatory fines, legal fees and operational downtime. According to IBM’s 2024 Cost of a Data Breach Report, the global average cost of a breach was $4.9 million.
There is also reputational damage to consider. Consumers are becoming worried about giving away personal data. According to SOTI’s 2025 retail report, 82% had at least one concern about entering personal details online or into an in-store device. An interesting duality has also emerged: 61% of consumers are worried about small retailers being able to keep their personal and payment data secure, yet major instances of data breaches are happening to large corporations.
What’s apparent is the need for device management and security for businesses of all sizes.
The Role of EMM
One of the most effective ways to mitigate these risks is through Enterprise Mobility Management (EMM). While the term may suggest mobile devices, modern EMM solutions manage a wide range of connected devices—from scanners to industrial printers, rugged devices, POS devices and tablets.
Here’s how EMM helps businesses strengthen their cybersecurity posture:
Click to expand and download
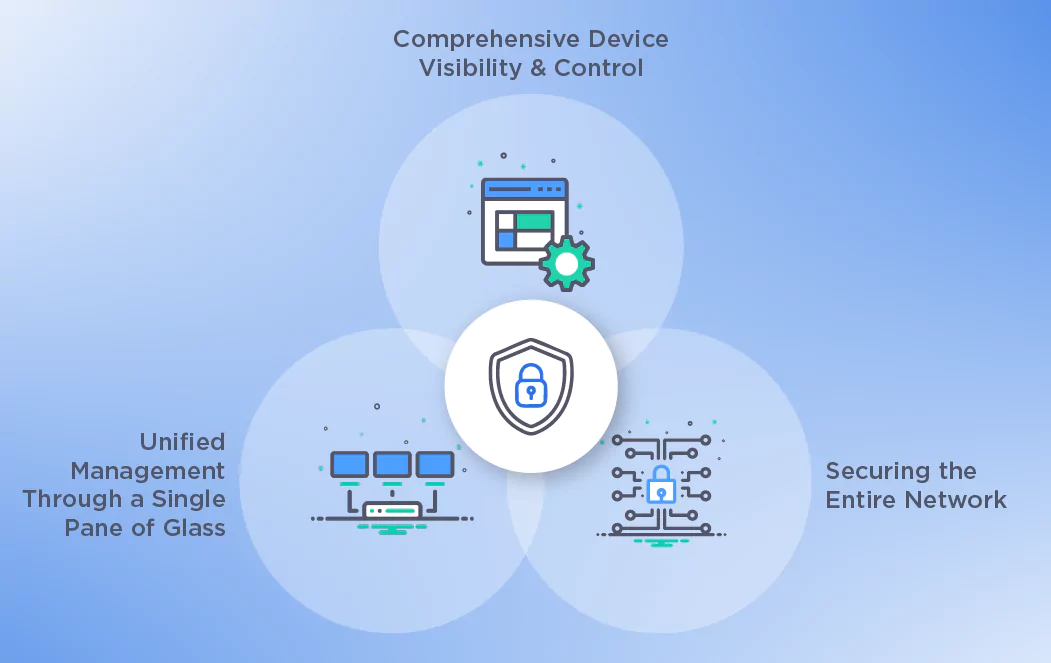
1. Comprehensive Device Visibility & Control
EMM solutions allow businesses to identify, monitor and manage every device connected to their network. This visibility is crucial in preventing unauthorized access and ensuring that all endpoints comply with security policies.
Whether it’s a mobile device used by a remote employee or a thermal printer used in a retail environment, EMM ensures that each device is accounted for and protected.
2. Unified Management Through a Single Pane of Glass
EMM solutions offer a centralized dashboard—often referred to as a “single pane of glass”—that allows IT teams to manage all devices and operating systems from one interface. This reduces complexity, minimizes the risk of oversight and enables faster response to potential threats.
By consolidating device management, businesses can enforce consistent security policies, deploy updates efficiently and maintain compliance with industry regulations.
3. Securing the Entire Network
Cybersecurity isn’t just about mobile devices. Printers, scanners, point-of-sale systems and other connected devices are often overlooked, but they can be just as vulnerable.
EMM solutions extend protection to these non-traditional endpoints, helping businesses secure their entire digital ecosystem. This holistic approach is essential in today’s interconnected environments, where a single compromised device can serve as a gateway for attackers.
Building a Cyber-Resilient Business
To stay ahead of cyber threats, businesses must adopt a proactive approach to security, including:
-
Investing in EMM Solutions: The SOTI ONE Platform is an innovative, integrated management solution that maximizes the ROI of your business-critical mobile devices and printers. Powered by actionable intelligence to help you make smarter, data-driven decisions, it reduces the cost, complexity and downtime of your mobile operations.
-
Train Employees: Human error and oversight are among the leading causes of data breaches. Attackers regularly prey on the emotions of people to get them to make rash decisions. Regular training on phishing, password protection, and device usage is essential.
-
Vet Third-Party Vendors: Ensure contractors and third-party partners meet your cybersecurity standards.
-
Update and Patch Regularly: By leveraging an EMM solution, you ensure that software is up to date and patched accordingly, limiting entry points for attackers.
-
Develop an Incident Response Plan: Be prepared to act quickly and decisively in the event of a breach. Have a plan in place to respond to a breach and limit damage.
Final Thoughts
The digital age offers incredible opportunities—but also unprecedented risks. As cyber threats grow more sophisticated, businesses must evolve their defenses. Enterprise Mobility Management is a critical component of that evolution, offering the visibility, control and flexibility needed to protect modern digital environments.
Cybersecurity isn’t optional. It’s a business imperative—and with the right tools and mindset, it’s a challenge that can be met head-on.