Using Bootstrap Token to Create Secure Tokens Automatically on macOS Devices
Before you begin
- This feature is supported on macOS devices running OS version 11 or later with macOS Agent 15.2.1 or later that are enrolled in SOTI MobiControl version 15.5.2 or later.
- Any macOS account is required to be secure token enabled.
About this task
In earlier macOS versions, the secure token was generated for local user accounts or Administrators, but mobile/network logins were blocked from logging into the device until the local user or Admin that held the secure token logged into the device. Apple automated the process of generating the secure token for mobile and network logins using the new bootstrap token concept starting with macOS Catalina. With bootstrap token, all mobile accounts that log in automatically get a secure token without having to hand one off manually.
For more information about secure token and bootstrap token, see Use secure token, bootstrap token, and volume ownership in deployments.
Procedure
- In a Device Group that contains macOS devices, right-click the name of the group and select Advanced Configurations.
- Select Apple from the drop-down list.
-
From the list of Advanced Configurations, click Bootstrap Token
(macOS only).
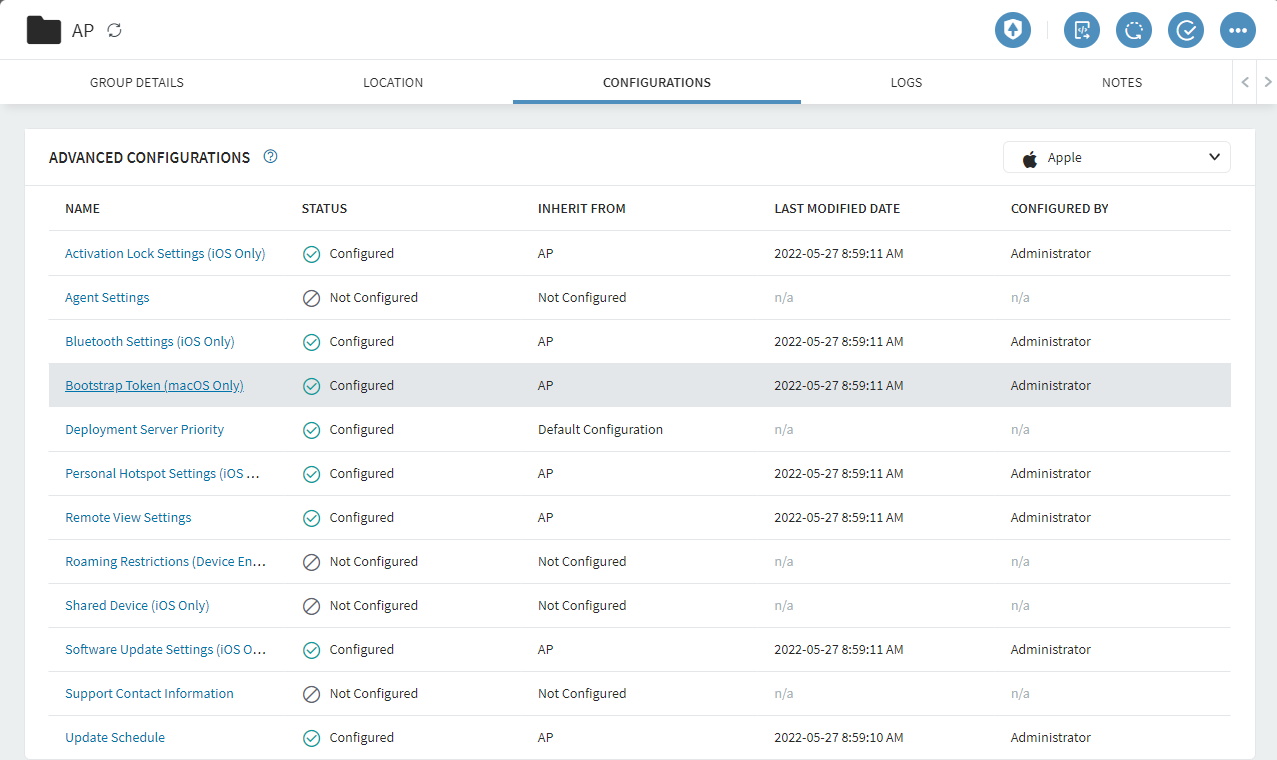
- Turn on the Bootstrap Token Options as described in Bootstrap Token Settings (macOS Only)
-
Click Save.
All applicable macOS devices in the Device Group are now enabled for bootstrap token. When the first admin account is created for devices in this group, the bootstrap token will be sent from the device to SOTI MobiControl for escrow. If you set up admin accounts previously for these devices, the token is passed at the next admin login event. When subsequent mobile accounts log into the device, the bootstrap token is retrieved from SOTI MobiControl and a secure token will be enabled on the account.
Monitoring Bootstrap Tokens on a Device
Procedure
- Click a device name to open its Device Information panel.
- Click the Logs tab. Any bootstrap token activity is logged as an event in the device log, which allows you to see the success or failure of token creation, requests, and deletion.
-
Click the Device Details tab. In the Security
section, SOTI MobiControl will show the current status of
the bootstrap token for this device:
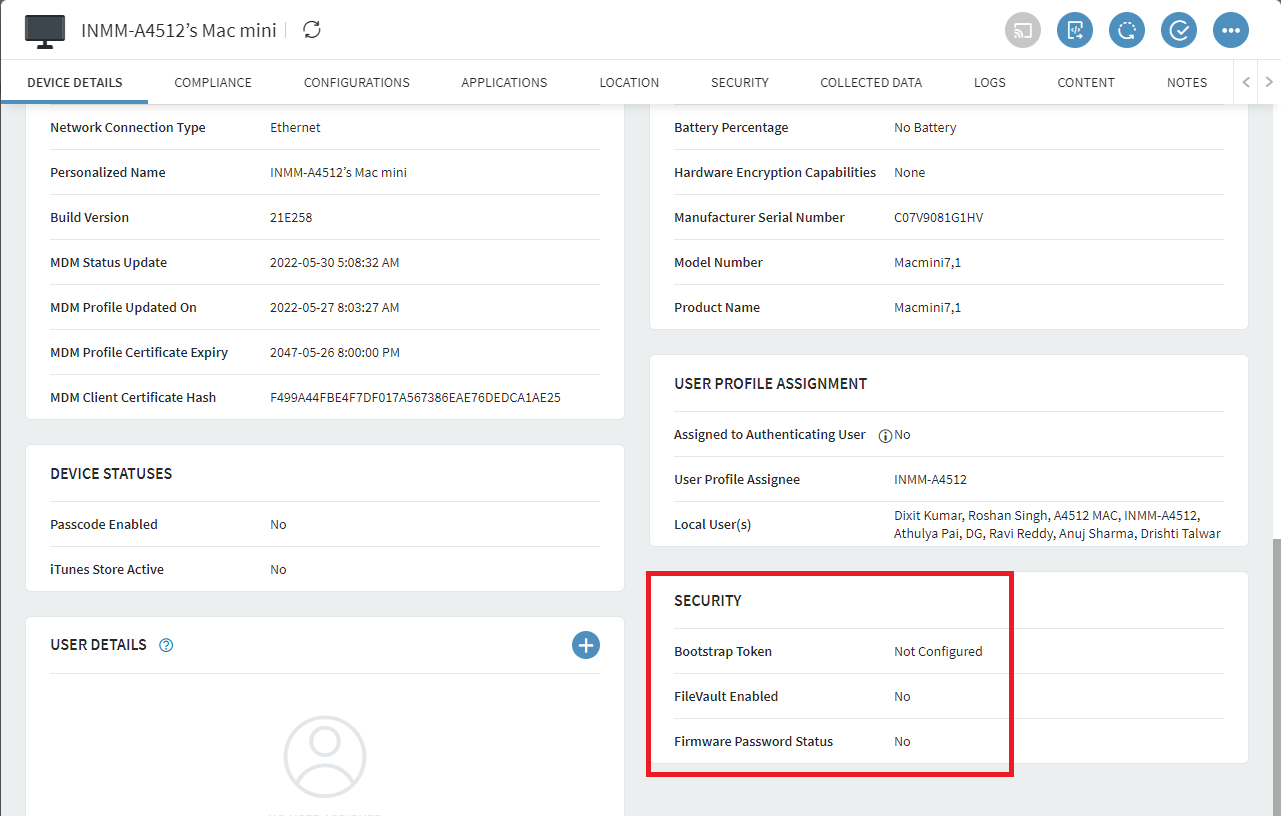
- NA: the device does not support bootstrap token.
- Not Configured: the device supports bootstrap token, but no token is escrowed in SOTI MobiControl yet.
- Configured: the device supports bootstrap token, and a token is currently escrowed in SOTI MobiControl.
Troubleshooting Bootstrap Tokens on Device Using Script Commands
About this task
| Command Description | Command Example |
| Generate bootstrap token and send to SOTI MobiControl server manually. | sudo profiles install -type
bootstraptoken |
| Remove bootstrap token and clear from SOTI MobiControl server manually. | sudo profiles remove -type
bootstraptoken |
| View status of bootstrap token. | sudo profiles status -type
bootstraptoken |
Validate the bootstrap token. When you trigger this
command on the device, a call is sent to the SOTI MobiControl server for
GetBootStrapToken. |
sudo profiles validate -type
bootstraptoken |
| List the users that hold a secure token. | sudo fdesetup list |
| Check secure token status for a particular user. | sysadminctl -secureTokenStatus
<UserName> |
| Enable and disable secure token. |
|