Creating a New Microsoft 365 App Protection Policy
Create an App Protection Policy to manage how Microsoft 365 data is accessed and secured on iOS and Android devices.
Before you begin
- This policy applies to iOS and Android devices.
- Your devices must have Microsoft 365 applications.
- SOTI MobiControl must connect to the Microsoft Endpoint Management service.
- Your devices must have the Intune Company Portal installed.
About this task
Procedure
- From the SOTI MobiControl web console main menu, select .
-
In the App Protection Policies section, select (add) to start the Create App
Protection Policy wizard.
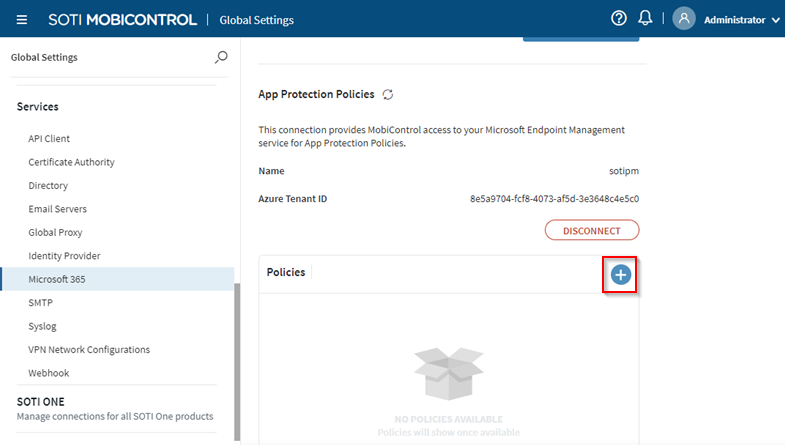
-
Choose to create an Android or Apple
(iOS) App Protection Policy.
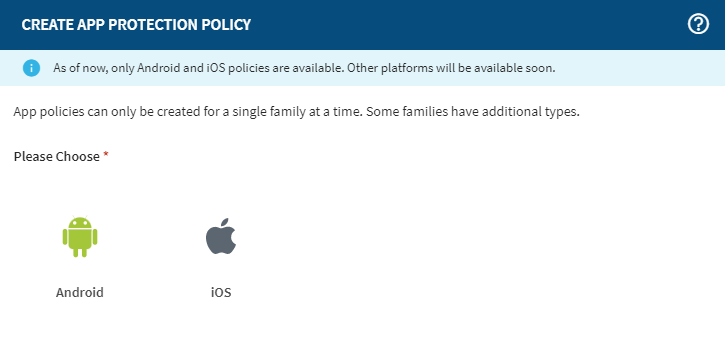
-
In the General tab, enter a Policy
Name and Description, and select
Next.
-
In the Apps tab, select (add) to view the first 50 available
applications. Use the Search apps field to search for
applications not listed in the first 50 applications. Select the required
applications and select Add.
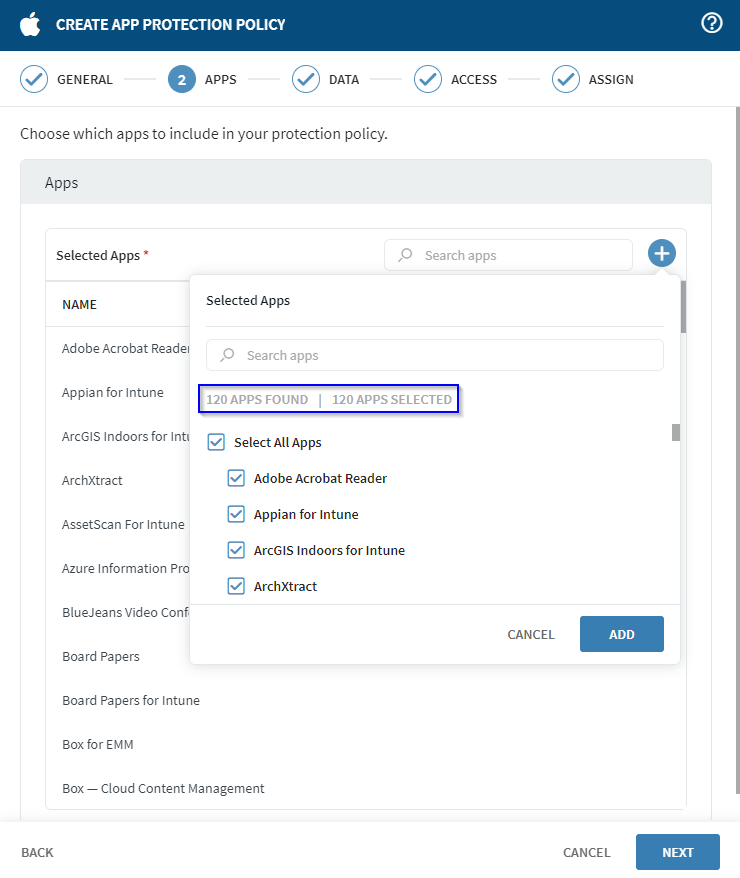 Tip: The information below the Search apps field displays the number of applications available and the number of applications selected.
Tip: The information below the Search apps field displays the number of applications available and the number of applications selected.When finished, select Next.
-
In the Data tab, select how to protect your Microsoft
365 apps' data:
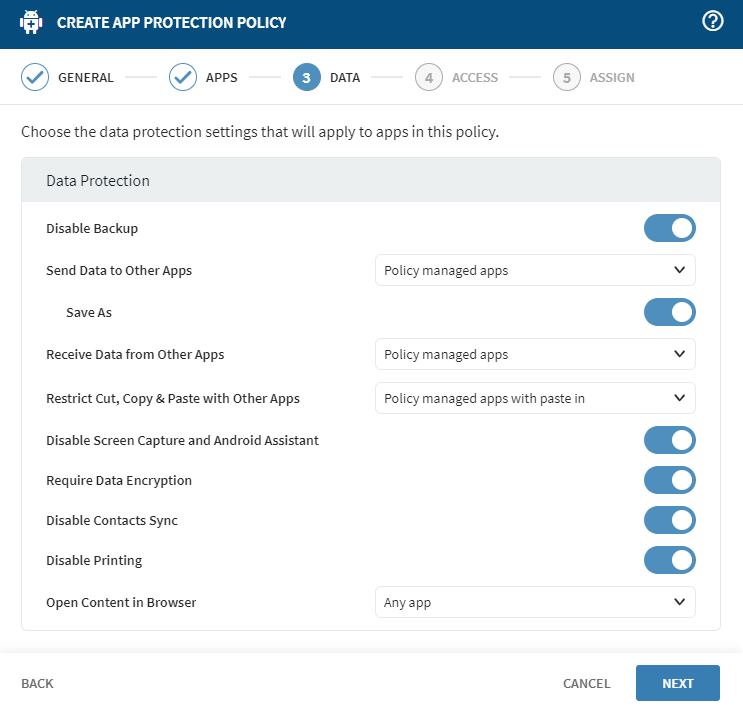
Data Protection Settings
Option Description Disable Backup Choose: - Block to disable backup of organizational data to Android backup services.
- Allow to enable backup. Personal and unmanaged data is unaffected.
Send Data to Other Apps Select the apps to which this app can send organizational data. Receive Data from Other Apps Select an option for apps this app can receive organizational data from: - None: Prevent receiving organizational data from any app.
- Policy managed apps: Only receive organizational data from policy-managed apps.
- All apps: Receive organizational data from any app.
Restrict Cut, Copy & Paste with Other Apps Block or allow these actions for use with any app, or restrict their use to apps that your organization manages. Disable Screen Capture and Android Assistant Enable or disable screen capture and Google Assistant app scanning capabilities when using a policy-managed app. Require Data Encryption Enable encryption of work or school data in this app. Intune uses an OpenSSL, 256-bit AES encryption scheme, and the Android Keystore system to securely encrypt app data. Data encrypts synchronously during file input/output tasks. Content on the device storage is always encrypted. Disable Contacts Sync Prevent policy-managed apps from saving data to the native Contacts and Calendar apps on the device. Disable Printing Prevent an app from printing protected data. Open Content In Browser Choose the apps that this app can open web content in. Select SOTI Surf as the only browser for web content, specify a different unmanaged browser, or allow any app to open web links. Tip: Hover over protection settings in the interface to learn more about its application in the policy.When finished, select Next.
-
In the Access tab, configure the PIN and credential
requirements for users to access the applications.
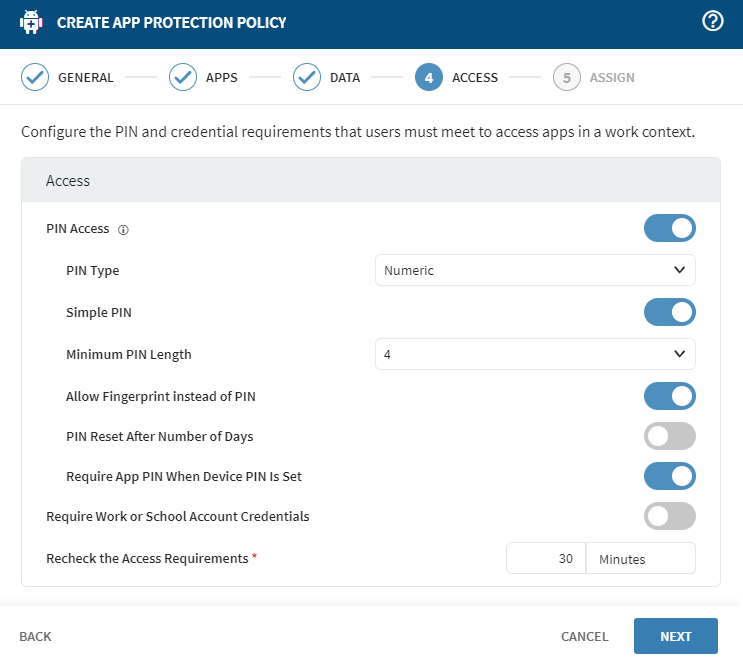
Access Settings
Option Description PIN Access If required, a PIN must be used to access the policy-managed app. Users must create an access PIN the first time they open the app.
PIN Type On iOS/iPadOS, Passcode requires the app to have Intune SDK version 7.1.12 or above. Numeric type has no Intune SDK version restriction.
Simple PIN Disabling the Passcode PIN type requires the passcode to have at least one number, letter, and special character.
Minimum PIN Length Specifies the minimum number of digits or characters required for the PIN. Allow Touch ID instead of PIN iOS 8+/iPadOS only.
Allow Face ID instead of PIN iOS 11+/iPadOS only.
PIN Reset After Number of Days Defines how many days a PIN remains valid before the user must create a new one. Require App PIN When Device PIN Is Set If disabled, an app PIN is not needed to access the app if the device PIN is set on an MDM enrolled device.
Require Work or School Account Credentials If enabled, access to the policy-managed app requires work or school credentials. If the PIN method is also required for access to the app, work or school credentials are required in addition to those prompts.
Recheck the Access Requirements The time, in minutes, that an app must be inactive before prompting a recheck of the access requirements (PIN, conditional launch settings, etc.). The value must be between 1 and 65535.
When finished, select Next.
-
In the Assign tab, select (add) to assign one or more
User Groups to the protection policy.
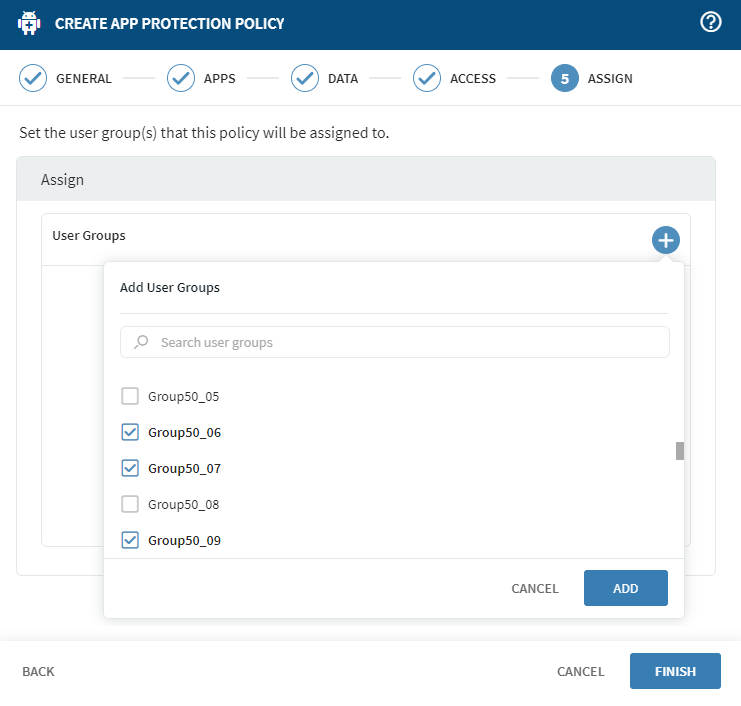
- Select Finish to complete and save your protection policy. The policy is active immediately for the assigned user groups.